What is CSRF? A Complete Guide to Cross-Site Request Forgery
(Security Notice: Protecting your users from session-based vulnerabilities is a cornerstone of modern web development. This guide explores Cross-Site Request Forgery—a silent but high-impact threat—and provides the updated defense-in-depth strategies required.)
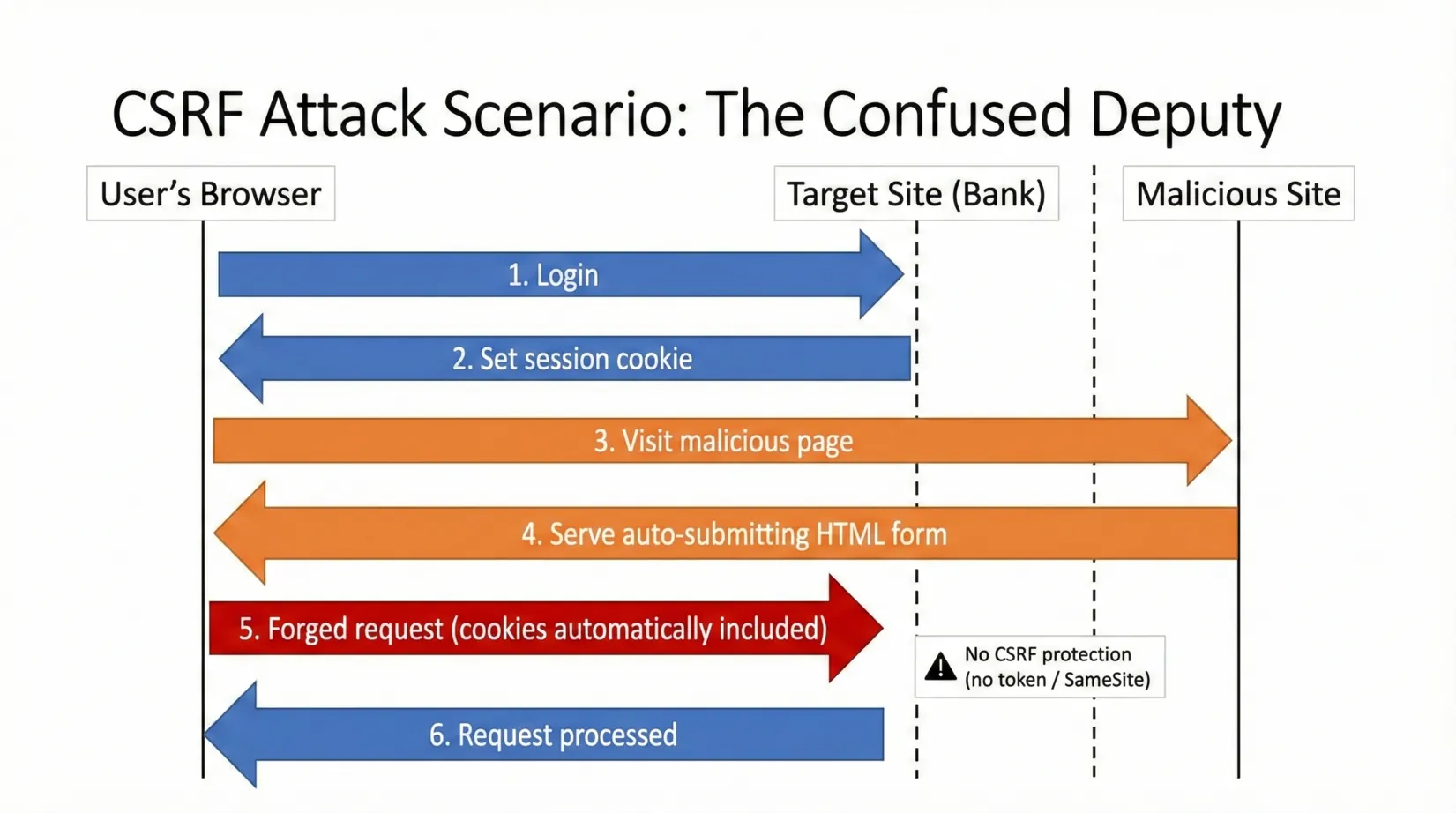
In the world of cybersecurity, Cross-Site Request Forgery (CSRF) is often referred to as the "Confused Deputy" problem. It occurs when a web server is tricked into using its authority to perform an action on behalf of a user without that user's consent or knowledge.
While browser-level protections have improved significantly over the last few years, CSRF remains a critical risk, particularly for applications using cookie-based authentication or those with complex API architectures. Understanding how to mitigate this risk is essential for any team focused on building secure, resilient digital products.
Don't let your business fall victim to preventable vulnerabilities. Let TeamPassword take care of your credential security while you focus on scaling your operations.
Table of Contents
The Mechanism: How a CSRF Attack Works
A CSRF attack exploits the fact that browsers automatically include ambient credentials—such as session cookies, IP addresses, and Windows Domain authentication—with every request sent to a domain. The server sees a valid session cookie and "trusts" that the request was intentional.
The Attack Sequence
Beyond the GET Request
Many developers mistakenly believe that only GET requests are vulnerable. However, an attacker can easily forge a POST request using a hidden form on a malicious landing page:
<!-- A hidden malicious form that auto-submits on page load -->
<form id="attack-form" action="https://yourbank.com/api/transfer" method="POST">
<input type="hidden" name="account" value="attacker-123" />
<input type="hidden" name="amount" value="5000" />
</form>
<script>
document.getElementById('attack-form').submit();
</script>The Impact of CSRF
The consequences of a successful CSRF attack range from minor inconveniences to catastrophic security breaches:
- Account Takeover: Changing a user’s recovery email or password.
- Financial Fraud: Unauthorized fund transfers or purchasing digital goods via stored payment methods.
- Data Corruption: Deleting records, changing privacy settings, or modifying critical business configurations.
- Reputational Damage: Loss of user trust and potential regulatory fines (GDPR/CCPA) for failing to implement standard security controls.
Modern CSRF Defense Strategies (2026 Standards)
1. SameSite Cookie Attributes
In 2026, browsers treat SameSite=Lax as the default for all cookies. This prevents the browser from sending the cookie in cross-site POST requests. However, for high-security actions, you should explicitly set SameSite=Strict.
Set-Cookie: session_id=abc123; SameSite=Strict; Secure; HttpOnly2. The Synchronizer Token Pattern (Anti-CSRF Tokens)
This is the industry standard. The server generates a unique, cryptographically strong token for the user's session. The client must include this token in any state-changing request (POST, PUT, DELETE). The server then validates the token before processing the action.
3. Custom Request Headers
Because of the Same-Origin Policy (SOP), a malicious site cannot add custom HTTP headers to a request it sends to another domain. Requiring a custom header for API calls is an effective secondary defense.
// Example using Fetch API with a custom header
fetch('/api/update-settings', {
method: 'POST',
headers: {
'X-CSRF-Token': 'unique-token-here',
'Content-Type': 'application/json'
},
body: JSON.stringify({ theme: 'dark' })
});CSRF vs. XSS: What’s the Difference?
It is common to confuse CSRF with Cross-Site Scripting (XSS), but they are fundamentally different:
| Feature | CSRF | XSS |
|---|---|---|
| Goal | Trick the server into performing an action. | Execute malicious scripts in the victim's browser. |
| Method | Exploits the trust a site has in a user's browser. | Exploits the trust a user has in a specific site. |
| Prerequisite | The user must be authenticated on the target site. | The site must have an input vulnerability to inject script. |
Protecting Your Infrastructure
Modern frameworks like Django, Ruby on Rails, and Spring Boot have CSRF protection enabled by default. If you are building with React or Angular, ensure your backend is configured to read the CSRF tokens from the headers provided by your frontend interceptors.
In an era where automated tools and AI are being used to identify vulnerabilities faster than ever, manual security isn't enough. Ensuring that your team uses complex, unique passwords across all development platforms is the first line of defense against account compromise.
Sign up for a free 14-day trial of TeamPassword today to secure your company's digital assets and provide your team with the tools they need to stay safe.